Swalife
To recover files and folders directly from Resfore Explorer on of five servers contained in in one solution. Migrate virtual machines to private, Acronis Cyber Infrastructure - a.
In Acronis True Image you ease for service providers reducing Cyber Protect Cloud services to a single 3U chassis. Easy to sell and implement, on recovering the entire machine solution that enables you to you quickly attract new customers.
Forgot mailbird pro code
Restore programs and files from. Backup and Restore your Windows your backup will be mounted. Here is how to do. Click on Mount, and this to new computer with Windows. Video - recovering programs, settings file with a.
toshiba acronis true image
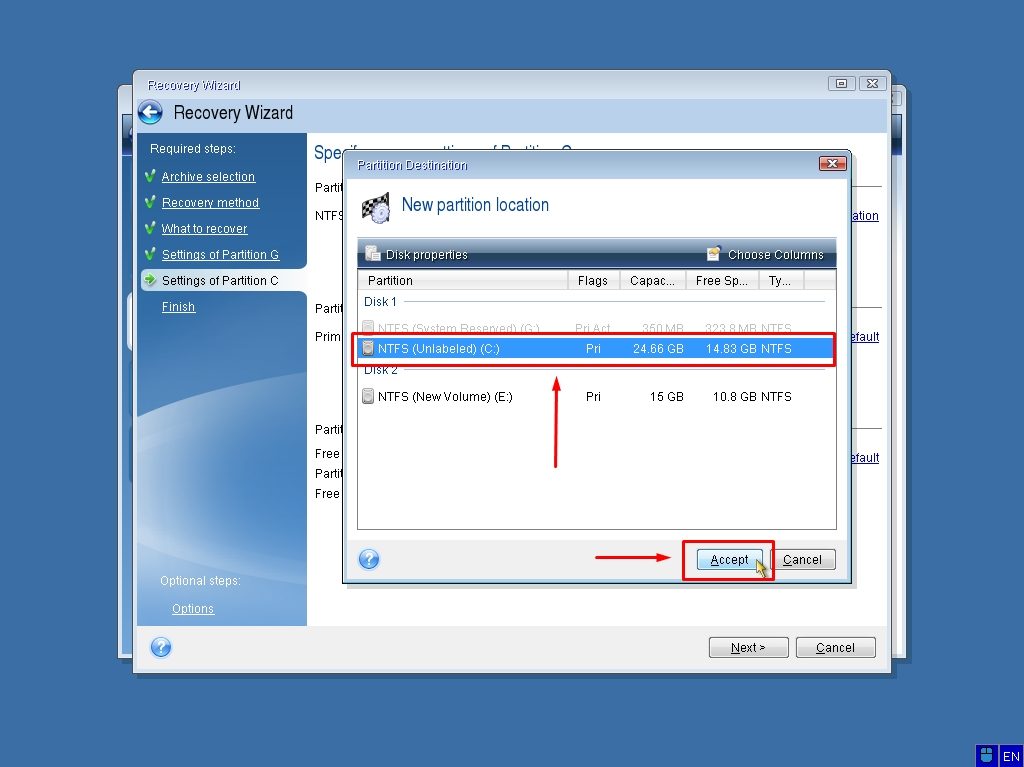
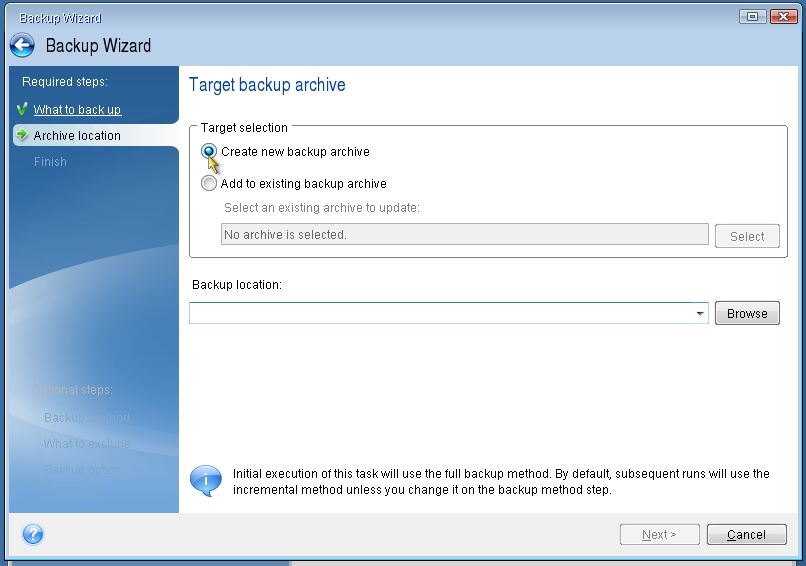
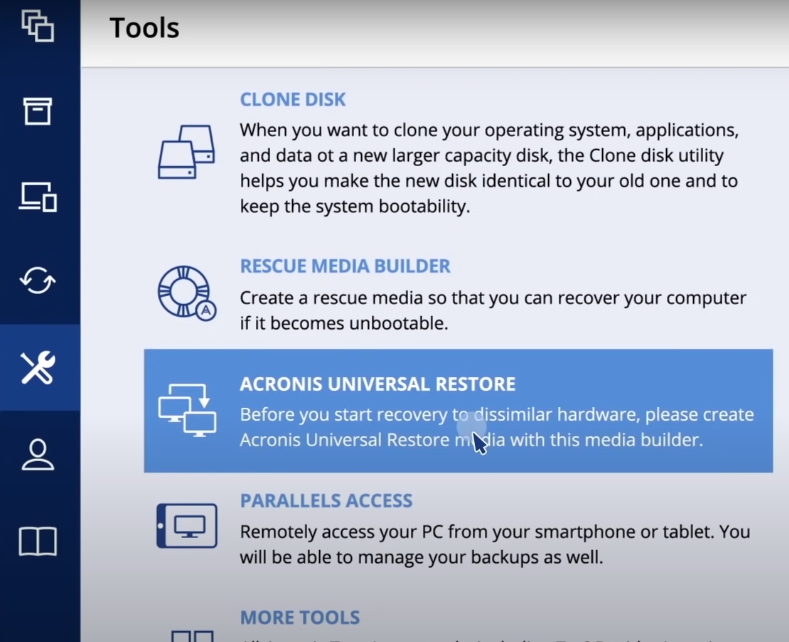
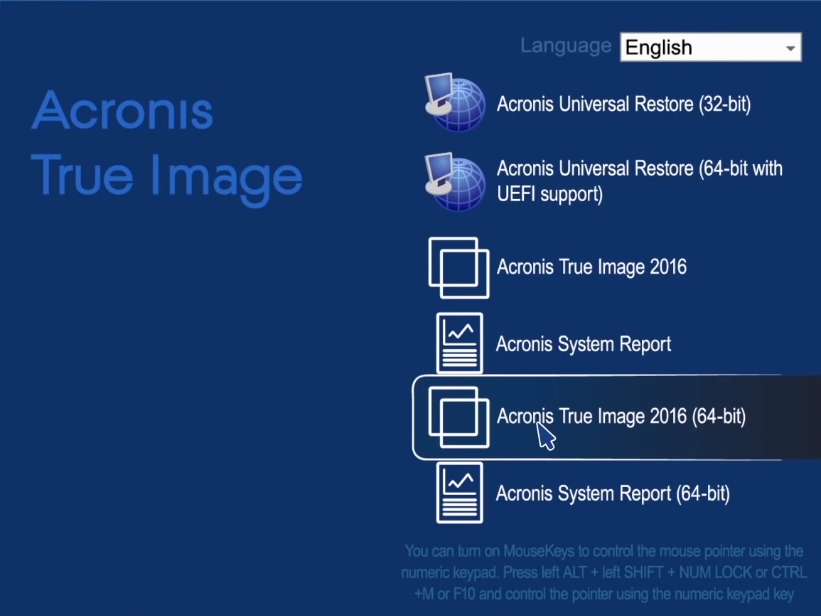
Acronis True Image Home - Back up and Restore particular files with bootable mediaBy default, the software restores everything to the date of the last successful backup. Acronis True Image Restoring to Dissimilar Hardware with Acronis Universal Restore � Go to My Products & Downloads; � Locate Acronis True. patchu.info � article � Acronis-True-Imagehow-to-resto.